Mind the CORS
Aug 24, 2023· ,,,·
0 min read
,,,·
0 min read
Matteo Golinelli
Elham Arshad
Dmytro Kashchuk
Bruno Crispo
Abstract
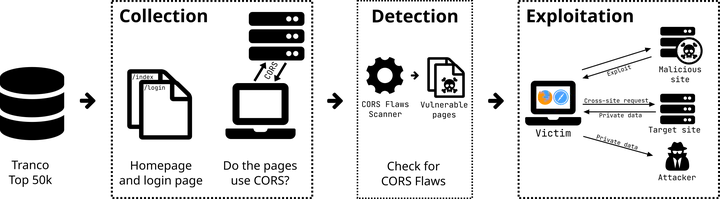
Cross-Origin Resource Sharing (CORS) is a mechanism to relax the security rules imposed by the Same-Origin Policy (SOP), which can be too restrictive for websites that rely on cross-site data exchange for their functioning. CORS allows trusting origins different from the website domain despite the presence of a strict SOP using a series of HTTP headers. This mechanism is supported by all modern browsers and is extensively adopted by websites. In CORS, servers are responsible for validating the value of the Origin header and deciding whether or not to trust it. For this reason, developers must be thorough in coding this process not to introduce security issues. We carried out a large-scale analysis on the Tranco Top 50k to measure the prevalence of various implementation flaws due to errors or simplifications in Origin validation and found that of the 6,862 websites using CORS, 2,014 (29.4%) have at least one flaw. We next exploit the vulnerabilities introduced by these CORS flaws in a realistic real-world scenario from the point of view of two attacker models with varying capability levels, evaluating the conditions necessary for a successful attack and its consequences. We show how these flaws enable attackers to perform Denial of Service and steal victims’ sensitive data and security tokens that can then be used to mount subsequent attacks. We conclude that CORS is an effective but complicated mechanism and its use should be carefully evaluated by website operators not to risk introducing severe security issues in their systems.
Type
Publication
The Fifth IEEE International Conference on Trust, Privacy and Security in Intelligent Systems, and Applications