Koney: A Cyber Deception Orchestration Framework for Kubernetes
Abstract
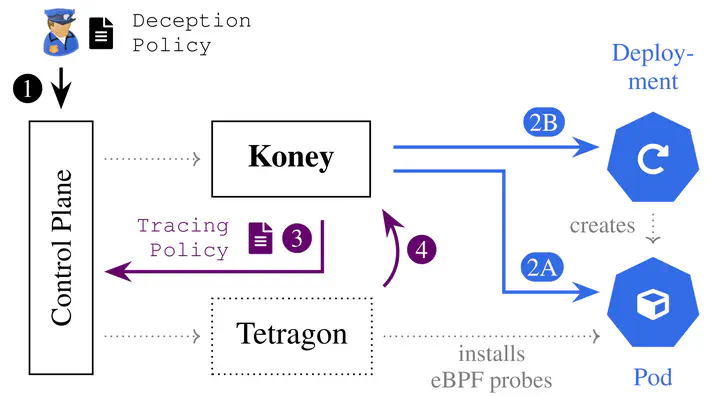
System operators responsible for protecting software applications remain hesitant to implement cyber deception technology, including methods that place traps to catch attackers, despite its proven benefits. Overcoming their concerns removes a barrier that currently hinders industry adoption of deception technology. Our work introduces deception policy documents to describe deception technology “as code” and pairs them with Koney, a Kubernetes operator, which facilitates the setup, rotation, monitoring, and removal of traps in Kubernetes. We leverage cloud-native technologies, such as service meshes and eBPF, to automatically add traps to containerized software applications, without having access to the source code. We focus specifically on operational properties, such as maintainability, scalability, and simplicity, which we consider essential to accelerate the adoption of cyber deception technology and to facilitate further research on cyber deception.
Type
Publication
4th Workshop on Active Defense and Deception (ADnD 2025) co-located with IEEE EuroS&P
Cyber Deception
Deception Policies
Honeytokens
Honeypots
Application Layer Deception
Runtime Deception
Operator Pattern
Kubernetes
Authors
CyberSecurity PhD Student
My main research interests include web security, with special focus on web caches and proxies.